The article examines crypto labels reader for blockchain technology is poised as the future of digital transactions, infusing trust, efficiency and transparency into supply chains. But blockchains alone cannot ensure the authenticity of physical goods. Crypto labels reader for cryptographic label technology will help solve the blockchains problem.
Keywords: blockchain, cryptographic, labels, reader, technology.
Blockchain has demonstrated its value in financial services and now presents a significant opportunity to drive savings in automotive, aviation, space and transportation industry with substantial transportation expenditures. These companies process thousands of freight transactions each day, and reconciling their shipment invoices against services with proper remittances is both laborious and costly. Blockchain has the potential to significantly reduce discrepancies in the process by enhancing transparency and improving accuracy in freight rates, shipment routing and invoice generation.

Fig. 1. Crypto Labels Reader
Through the global supply chain, products often change hands repeatedly before reaching their destination. Counterfeits can be introduced at any point along the way. Cryptographic Label Technology (CLT) for blockchain technology is poised as the future of digital transactions, infusing trust, efficiency and transparency into supply chains. But blockchains alone cannot ensure the authenticity of physical goods. CLT will help solve the blockchains problem. Components of the CLT are Crypto Labels (CL) and a Crypto Labels Reader (CLR).
Main part
The CLR [1] contains a microcontroller, nuclear magnetic resonance (NMR) scanner/reader and NFC (Near Field Communication) Reader, cellular modem (see Fig. 2)
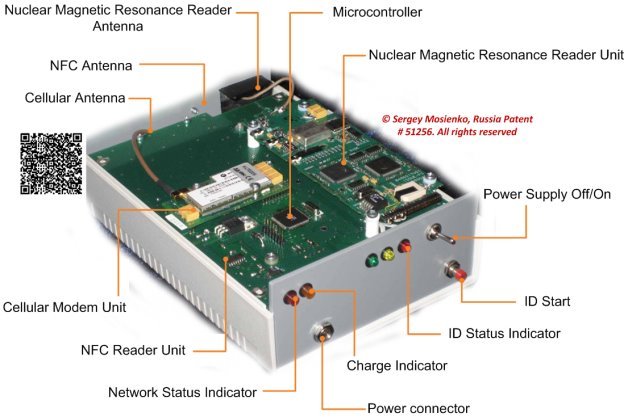
Fig. 2. Crypto Labels Reader
NMR Scanner for authenticating and/or identifying of Crypto Labels for space, aviation, automotive, defense devices comprise a units generating either continuous or pulse, either modulated or non modulated emitted radiation in the radio frequency band, including a generator of continuous or pulse modulated or non modulated radio frequency signal and an emitting probe head or coil, transforming it into electromagnetic radiation, and a system for detection of the re-radiation emitted by the resonant substance in response to the radio frequency radiation, including receiving probe head or coil and detection device with a registration device determining presence of the re-radiation from the resonant substance. The CL [2] consist the NFC-chip, antenna and magnetic resonance metal-transponder (MRMT) at insulation on which materials are deposited nuclear magnetic resonance in ferromagnets, or antiferromagnets, or ferrimagnets, or nuclear quadrupole resonance, or very low field electron spin resonance, or said resonance phenomenon is due to electric/magnetic dipole or tunnel transitions between Stark-Zeeman sub levels, or any combinations or aforementioned phenomena. СLs, tamper-proof digital fingerprints, to be embedded into products, or devices of products, and linked to the blockchain. These fingerprints can take many forms such as tiny NFC-chips, but when they are tied to a blockchain, they represent a powerful means of proving a space, aviation, automobile and defense devices authenticity. These СL’s pave the way for new solutions that can combat fraud and protect consumers.
How is it working?
The entire CLT or Crypto Labels System (CLS) consists of data carriers (crypto labels, for instance) attached to the objects of interests at their manufacturing and distribution centers (plants, storehouses, customs warehouses etc.), crypto labels readers of the aforementioned data carriers (at inspection points, stationary or hand-held) containing cellular modem allowing connection to global network and databases (certain serevr-localized or delocalized — cloud-based).
Each object automotive, aviation, space or defense industry of interest should be marked by a certain data carrier — crypto labels. Crypto labels contains information on an object, its manufacturing features (origin, batch, time stamp) and destination (where the object should be delivered etc.). The marking occurs at manufacturing facilities, in distribution centers etc. The latter facilities form corresponding data base which stores precise conformity of objects and data attributed to these object at marking.
At inspection points crypto labels readers read information from crypto labels and transfer this information to corresponding data bases for checking its validity and providing tracking data. It is very important that information read from crypto labels will not be distorted/counterfeited over all network transactions. Of course, databases themselves must be highly secured.
The blockchain technology provides unique uncompromised abilities to protect secure data transfer and processing. Thus, blockchain perfectly protects this part of the crypto labels system.
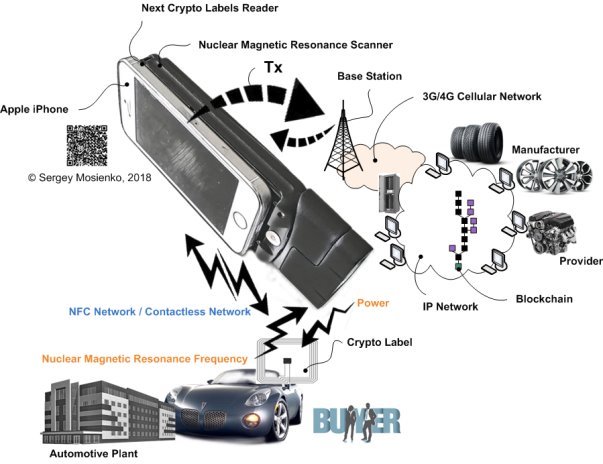
Fig. 3. Next Crypto Labels Reader
However, all smart blockchain technologies will be absolutely useless in the case when counterfeiters will compromise/fake the data carrier (crypto labels) itself. Let us suppose a counterfeiter will duplicate the adhesive crypto label attached to an authentic object, for instance, brake pads for car and then attach it to the faked object (brake pads for car). Indeed, both crypto label (data carrier) and data base contain full information on authenticity of that object (brake pads for car). The crypro labels reader in the inspection point will read data form an unknown object (brake pads for car) and then secure transfer it to data base using advanced blockchain technology. And inform the inspector that the object (brake pads for car) is authentic. Sounds good, doesn’t it?
Let us suppose that next time another inspector will read another object carrying the same data. And then secure transfer it to the data base. Which response will it get from the data base? Is that object authentic? Data base will inform on duplicated data (the object was checked before) and put the authenticity of this object under question. May we call the second object not authentic (or having other destination etc.)? Which one of these two (three, four etc.) of these objects was really authentic? Nobody knows!
That is why the blockchain technology only cannot provide real crypto labels system. It is absolutely obvious that the data carrier must be physically protected from duplications/imitations. The crypto labels reader at the inspection point must be confident that the data carrier on an object is original, i.e. not faked. Thus, the reading device must have some tools for machine recognition of the authenticity of data carrier.
NMR Scanner provides perfect tools for such recognition. Indeed, magnetic resonance metal-transponder (MRMT) provides machine readable invisible tag for physical anti-counterfeiting protection crypto labels (crypto chip) of objects. Each object/data carrier is reliably protected from any unauthorized duplication. For working 10 years in anti-counterfeiting and brand protection business, magnetic resonance metal-transponder having been never compromised, i.e. totally faked or somehow imitated. Magnetic resonance metal-transponder for crypto labels (crypto chip) in combination with blockchain perfectly matches all targets of crypto labels system. In the proposed version of crypto labels system each data carrier it tagged by magnetic resonance metal-transponder for crypto labels. The crypto labels reader in the inspection point first checks the crypto labels (data carrier) for its authenticity by magnetic resonance metal-transponder for crypto labels.
It takes a couple of seconds or even less. In the case the data carrier (crypto labels) is authentic; the crypto labels reader (inspection device) reads data and then securely transfers them (together with the attribute “authentic”) through network to data base. In the case the crypto labels is found to be faked, the crypto labels reader may inform authorities and/or data base on appearance and location of the faked/compromised object.
The smartphone transmits the information data received from the Crypto Labels via the base stations of the cellular network to the distributed database servers blockchains technology. The blockchain gives internet users the ability to create value and authenticates digital information crypto labels.
Developing digital identity standards is proving to be a highly complex process. Technical challenges aside, a universal online identity solution requires cooperation between private entities and government. Crypto labels reader for cryptographic label technology will help solve the blockchains problem.
Conclusions
Blockchain and crypto labels technologies are the two keys to a more advanced, democratic and independent society. Blockchain technology has become a force that is giving rise to new, decentralized structures that will shape future societies and economies. Thus, proposed combination of crypto labels technology and blockchains technologies, in sum, creates the only crypto labels system which may be called “secure”.
References:
1. Patent of the RU No.72592 — Modern Identification Wireless Reader./Mosienko S. A.
2. Patent of the RU No.51256 — Protected from fake non-contact smart card microcontroller./Mosienko S. A.







