The idea of user-based, content-based and demographic-based recommendation mechanism is adopted to analyze and calculate these real data and extract the recommendation results to recommend to users to complete personalized movie recommendation.
Keywords: demographic-based algorithm; recommendation system; Big Data; implementation
Introduction
With the continuous development of information technology and the rapid popularization of intelligent terminal equipment, the difficulty of Internet users to obtain information is also gradually reduced. At the same time, people also pay more and more attention to the spiritual level of demand, film and television resources as a good way of spiritual entertainment, widely welcomed by people. Although there are many film and television resource providers on the Internet, users can easily obtain film and television resources, but users also need to consume a lot of time to screen their favorite movies. In order to solve this problem, many content providers have started to build their own personalized recommendation systems [1].
For clustering by demographic data, it is natural to use the k-means method, since in this case each cluster is determined by its center point and, as a result, is well interpreted. The distance from the object (user) to the center of the cluster can be determined, generally speaking, in an infinite number of ways. It is customary to use the Euclidean metric in the feature space [2].
Research Background and Significance
According to CNNIC China Internet Development statistics analysis, as of December 2018, the number of Internet users in China is up to 829 million, and the Internet penetration rate is as high as 59.6 %. Among them, the proportion of users using mobile phones to surf the Internet has reached 98.6 % (Figures 1–2).
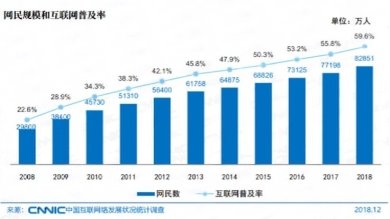
Fig. 1. Size of Internet users and Internet penetration rate
Under the background that more than half of the people in China are netizens, traditional media also begin to provide network services. For example, CCTV launched its exclusive CCTV video client and Hunan SATELLITE TV's Mangol TV. People also gradually reduce their dependence on traditional media (such as TV, cinema, etc.) and choose to use network platforms in most cases.
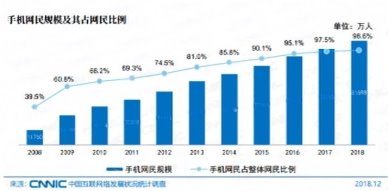
Fig. 2. Scale of mobile Internet users and their proportion in Internet users
With the continuous improvement of network bandwidth and storage system capacity, the amount of information on the network shows an explosive growth trend, and netizens can access a large number of film and television resources at any time. Although massive information can meet people's demand for information in the information age, the problem that follows is how users can quickly find resources that meet their needs.
System Development Tools
Since the appearance of recommendation engine, recommendation based on user information has been widely used. The algorithm uses the attribute values of related users to find the correlation between different commodities, and the system recommends similar commodities to users according to the previous historical preferences of similar users [3].
As the foundation of Big Data, it perfectly abstracts the overall picture of a user's information, providing sufficient data basis for further accurate and rapid analysis of important information such as user behavior habits and consumption habits.
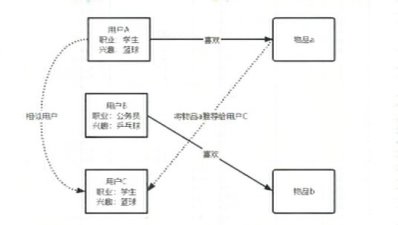
Fig. 3. Implementation process
Second, the implementation process (Figure 3):
— The system will first model according to the user's attributes, such as the user's age, gender, interests, occupation and so on.
— The similarity between users is calculated based on these characteristics. For example, the system calculates that user A and user C are similar.
— Would recommend items that A likes to C.
System Analysis and Design
It can be seen from the Figure 4 that the personalized recommendation system consists of three parts: users, database and recommendation algorithm. The database is used to store user and movie information and user behavior. When the user logs in, the recommendation system will read user and movie information and behavior records from the database, and the recommendation algorithm will carry out a series of calculations and push the results to the user [4].
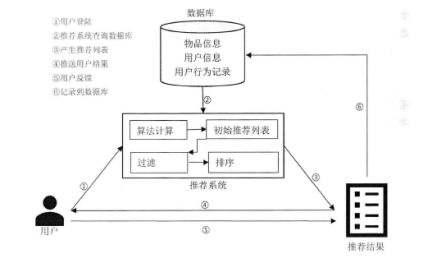
Fig. 4. Recomendtation system structure
On the whole, this recommendation system can be divided into three layers, including the presentation layer, data access layer and business logic layer. Such layering enables the layers to be independent of each other, so that developers at each layer can independently develop the functionality of their own layer as long as they understand the interfaces of each layer. When the system needs to be upgraded or changed, it only needs to find the corresponding code of each layer for modification, which makes the upgrade and maintenance of the whole system more convenient. Such architecture can well achieve the functions of high cohesion, low coupling and logical reuse.
The presentation layer can provide users with a human-machine interface that is convenient for users to interact with the system, so that users can use the services provided by the system well and achieve user needs. This system provides the interface to the user, including: login interface, movie search interface, main function interface, movie list interface, movie details interface, personal collection interface, history play interface, similar recommendation interface, personalized recommendation interface.
The data access layer is used to store data and read the stored data, submit data reading in the database to the business logic layer, and then send the calculated result information back to the database to keep the database updated in real time. The table of this layer data design includes movie information, user information and similarity matrix between movies.
The business logic layer connects the presentation layer with the data access layer, which is at the core of the architecture.
References:
- Gormley, Isobel & Murphy, Thomas. (2009). A grade of membership model for rank data. Bayesian Analysis. 4. 265–296.
- Li, Bo & Fan, Zhang-Tao & Zhang, Xiao-Long & Huang, De-Shuang. (2019). Robust dimensionality reduction via feature space to feature space distance metric learning. Neural Networks. 112.
- Sousa, Elaine & Jr, Caetano & Traina, Agma & Wu, Leejay & Faloutsos, Christos. (2007). A fast and effective method to find correlations among attributes in databases. Data Min. Knowl. Discov.. 14. 367–407.
- Li, Min & Zeng, Yingming & Guo, Yue & Guo, Yun. (2020). A Movie Recommendation System Based on Differential Privacy Protection. Security and Communication Networks. 2020. 1–10.







