In given article the analysis of research works results on studying and application of the Session Initiation Protocol (SIP) is provided in works of foreign researchers.
Key words:protocol, buffer overflow, configuration, SIP server, principle.
Initially we need to make an overview of researched area. There are [1] thorough surveys and all the publications divided into some categories: overviews, field studies and analysis, performance analysis, authentication protocols, architecture, middle boxes, instruction detection, miscellaneous.
Figure 1 shows numerical relation between the categories.
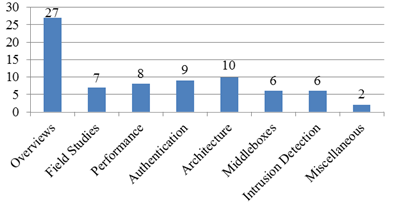
Fig. 1. Relation between researched categories in VoIP area
According to [1] Wieser et al. [2] extend the PROTOS testsuite [3] with the a SIP-specific analysis fuzzing module. They then test their system against a number of commercial SIP implementations, finding critical vulnerabilities in all of them.
Berson [4] conducted an evaluation of the Skype system under contact by Skype itself, allowing him access to the source code. The evaluation focused primarily on the cryptographic protocols and algorithms used, and did not discover any significant issues. Baset and Schulzrinne [5] performed a black-box analysis of Skype, identifying some characteristics of the underlying protocol. Biondi and Desclaux [6] dissected the Skype binary in detail, exposing the extensive anti-debugging mechanisms built in the program. Their analysis identified a small number of vulnerabilities (including a butter overflow).
Thermos and Hadsall [7] survey a number of Small Office Home Office (SOHO) VoIP gateways and related equipment, as provided by 3 different commercial VoIP providers with different corporate profiles and customer bases. Their analysis looks at four key factors: manageability, node security, signaling security, and media security. They find numerous problems, including insecure access to the web-based management interface, default passwords and inappropriate services, lack of encryption to protect signaling and media, and low-level implementations issues (e.g., presumed buffer overflow vulnerabilities and fuzzing-induced crashes). A similar survey by Scholz [8] looks at protocol and device problems and vulnerabilities at a medium-size German ISP with high rate of VoIP adoption. He focuses on intentional and unintentional denial of service attacks, problems are found, including DoS through call forks, misconfigured devices, and lawful-interception evasion, among others.
INRIA has been conducting a multi-thrust effort to apply testing and fuzzing toward identifying vulnerabilities in SIP protocols [9], implementations [10] and deployed systems. It is worth noting that this work has resulted in a number of vulnerability disclosures in the Common Vulnerabilities and Exposures (CVE) database and elsewhere.
Reason and Messerchmitt [11], in one of the earliest works on the subject of the performance impact of security mechanisms on VoIP, looked specifically at the error-expansion properties of encryption and their effect on voice quality. They analytically derive the post-decryption Bit Error Rate (BER) relative to the pre-encryption BER for block and stream ciphers, and analyze the effect of error-expansion mitigation techniques, such as the use of forward error correction, on quality of service. They discuss an error-robust encryption scheme that is analogous to self-synchronizing ciphers.
Elbayoumi and Shepherd [12] conduct a performance comparison of block and stream cipher encryption in the context of securing VoIP calls. They analyze the impact of each on end-to-end delay and subjective quality of perceived voice. A broader view at several performance-impacting parameters is given by the same authors in a concurrent paper at the same journal [13].
Salsano et al. [14] give an overview of the various SIP security mechanisms (as of 2002), focusing particularly on the authentication component. They conduct an evaluation of the processing costs of SIP calls that involve authentication, under different transport, authentication and encryption scenarios. They show that a call using TLS and authentication is 2.56 times more expensive than the simplest possible SIP configuration (UDP, no security). However, a fully protected call takes only 54 % longer to complete than a configuration that is more representative than the basic one but still offers no security; the same fully-protected call has the same processing cost if it is transported over TCP with no encryption (TLS). Of the overhead, approximately 70 % is attributed to message parsing and 30 % to cryptographic processing. With the advent of Datagram TLS (DTLS) [15], it is possible that encryption and integrity for SIP can be had for all configurations (UDP or TCP) at no additional cost [16].
Eun-Chul et al. [17], evaluate via simulation the costs of different security protocols (TLS, DTLS and IPSec) with respect to call setup delay using different transport protocols (TCP, UDP and SCTP). They conclude that the most efficient combinations, DTLS/UDP and IPSec/UDP, approximately double the call setup delay. However, since the analysis is purely simulation-based, their results are sensitive to the configured relative costs for processing the various protocols.
Shen et al. [18] also study the performance impact of using TLS as a transport protocol for SIP. In their experiments using a testbed, they use profiling at various system levels (application, library, and kernel), and decompose the costs at a fine level of granularity. They determine that use of TLS can reduce performance by a factor of up to 20 (when compared with the unsecured SIP-over-UDP). The main overhead factor is the cost of RSA signatures during session negotiation, while symmetric key operations impose a relatively small cost. They recommend that operators amortize the setup cost over long-lived connections. Finally, they provide a cost model for provisioning SIP-over-TLS servers, predicting an average performance overhead of 15 % under a suggested system configuration.
Buschel [19] argues for integrated authentication between User Agents and all elements of a SIP infrastructure. Cao and Jennings [20] propose a new mechanism for authenticating the responding user's identity in SEP without exposing said identity to untrusted intermediate elements. Their scheme requires additional headers in SIP messages, and has not been implemented or evaluated.
Insu and Keecheon [21] propose a secret key based mechanism to reduce the performance requirements of using public key certificates to protect signaling (e.g., with TLS) in an enterprise VoIP environment.
Schmidt et al. [22] suggest that administration overheads for implementing strong authentication in SIP could be lowered by grouping users with the same function or role (e.g., agents in a calling center). They propose a proxy-based mechanism for implementing a form of «certificate sharing» among a group of users, without exposing the corresponding private key to any of them. They demonstrate feasibility of the scheme by implementing it in the NIST SIP proxy, with no further evaluation.
Wang and Zhang [23] discuss an authentication and key agreement mechanism for SIP that uses certificate-less public-key cryptography.
Singh and Vuong [24] use a mobile agent framework to collect and correlate events from various network components, toward detecting a number of attacks. The stated advantages of their approach are that it does not require a new protocol for exchanging event information and that mitigation and recovery capabilities can be implemented by extending the framework and the agents, with no changes to the VoIP protocols. They also propose using user behavior profiles to detect anomalous behavior. They describe the operation of their system in a number of attack scenarios, including protocol-based denial of service, call hijacking, packet flooding, and abnormal call patterns.
Casola et al. [25], [26] suggest the use of a policy-based approach to design secure VoIP infrastructures. The policies express security goals in measurable terms; suggested infrastructure designs can then be evaluated against these policies to determine whether the goals are met to an acceptable degree.
Niccolini et al. [27] design an intrusion detection/intrusion prevention system architecture for use with SIP. Their system uses both knowledge-based and behavior-based detection, arranged as a series in mat order. They develop a prototype implementation using the open-source Snort IDS. They evaluate the effectiveness of their system in an attack scenario by measuring the mean end-to-end delay of legitimate SIP traffic in the presence of increasing volumes of malformed SIP INVITE messages.
Rieck et al. [28] apply machine learning techniques to detecting anomalous SIP messages, incorporating a «self-learning» component by allowing for periodic re-training of the anomaly detector using traffic that has been flagged as normal. The features used for clustering are based on n-grams and on tokenization of the SIP protocol. To prevent training attacks, wherein an adversary «trains» the anomaly detector to accept malicious inputs as legitimate, they employ randomization (choosing random samples for the training set), sanitization, and verification (by comparing the output of the new and old training models). Their experimental prototype was shown to handle 70 Mbps of SIP traffic, while viding a 99 % detection rate with no false positives.
Reynolds and Ghosal [29] describe a VoIP-aware middle box architecture that integrates the enterprise firewall, media gateway, and intrusion detection facilities to allow the secure operation of dynamic VoIP applications. The problem of firewall and NAT traversal by VoIP protocols has been the subject of some research [30], generally involving some kind of signaling (whether in-band or out-of-band) between the end-device and the middle box.
Gurbani et al. [31] propose an mechanism whereby proxies create an overlay network between user agents. This network is used for rendezvous/coordination purposes only. Once user agents establish a session, the proxies become transparent traffic forwarders, with the user agents communicating over an end-to-end secure session. This approach allows users to communicate without exposing (as much) private information to proxies, at the cost of requiring a PKI and a new message extension.
Relying on the foregoing facts, one of the main and little studied problems in the area of VoIP signaling is defining SIP server's parameters and its' influence on the performance characteristics.
Thereby, research's object can be defined as SIP server. Research's subject is distribution parameters of arrival and service rate.
Research's goal is to develop methodology of analyzing real network SIP equipment and to define distribution parameters and distribution laws arrival and service rate and their impact on server's behavior using the methodology.
Conclusion
Based on the overview of researched area we arrive at a conclusion at the question of real SIP server's investigation is crucial and important but still little studied so the work in this area could be helpful for comprehension of operational processes elapsed abroad «black box» equipment. There's also requirement in development of methodology for such research. The methodology will include statistical analysis of real network and construction of a model based on the analysis. Consequently, the scientific novelty of the research is among these two points.
References:
1. A. Keromytis. A Comprehensive Survey of Voice over IP Security Research, Columbia University Computer Science Technical Re-ports, USA 2010.
2. C.Wieser, M. Laakso, and H.Schulzrinne, “Security Testing of Sip Implementation”, Tech.Rep.CUCS-024–03, Columbia University, Department of Computer Science, 2003.
3. R.Kaksonen, M. Laakso, and A.Takanen, “Software Security Assessment through Specification Mutations and Fault Injection”.
4. T.Berson, “Skype Security Evaluation”, October, 2005.
5. S. A. Baset and H.Schulzrinne, “An Analysis of the Skype Peer-to-Peer Telephony Protocol”бшт Proceedimgs of IEEE INFOCOM, April, 2006.
6. P.Biondi and F.Desclaux, “Silver Needle in the Skype”, in Black Hat Europe conference, March, 2006.
7. P.Thermos and G. Hadsall, “Vulnerabilities in SOHO VoIP Gateways”, in Proceedings of the 2nd VoIP Security Workshop, June, 2005.
8. H.Scholz, “Attacking VoIP Networks”, in Proceedings of the 3rd Workshop on Security Voice over IP, June, 2006.
9. H.Abdelnur, R,State, and O.Festor, “Fuzzing for Vulnerabilities in the VoIP space”, in Proceedings of the 17th Annual Conference of the European Institute for Computer Anti-Virus Research (EICAR), May, 2008.
10. H.Abdelnur, R.State, and O.Festor, “KiF: A stateful SIP Fuzzer”, in Proceedings of the 1st International Conference on Principles, Systems and Applications of IP Telecommunications, pp.47–56, July, 2007.
11. J.Reason and D. Messerschmitt, “The Impact of Confidentiality on Quality of Service in Heterogeneous Voice over IP Networks”, in Proceedings of the IEEE Conference on Management of Multimedia Networks and Services, pp.175–192, November,2001.
12. A. D. Elbayoumy and S.Shepherd, “Stream or Block Cipher for Securinf VoIP≤”, International Journal of Network Security, vol.5, pp.128–133, September, 2007.
13. A. D. Elbayoumy and S.Shepherd, “A Comprehensive Secure VoIP Solution”, International Journal of Network Security, vol.5, pp.233–240, September, 2007.
14. S.Salsano, L.Veltri, and D.Papalilo, “SIP Security Issues: The SIP Authentification Procedure and its Processing Load”, IEEE Network, vol.16, pp.38–44, Nov/Dec 2002.
15. N.Modadugu and E.Rescorla, “The Design and Implementation of Datagram TLS”, in Proceedings of the ISOC Symposium on Network and Distributed Systems Security (NDSS), February, 2004.
16. E. T. Lakay and J. I. Agbiniya, “Security Issues in SIP Signaling in Wireless Networks and Services”, in Proceedings of the International Conference on Mobile Business, pp.639–642, July, 2005.
17. C.Eun-Chul, C.Hyoung-Kee, and C.Sung-Jae, “Evaluation of Security Protocols for the Session Initiation Protocol”, in Proceedings of the 16th International Conference on Computer and Networks (ICCCN), pp.611–616, August,2007.
18. C.Shen, E.Nahum, H,Schulzrinne, and C. P. Wright, “The Impact of ЕДЫ on SIP Server Performance”, in Proceedings of the 4th Annual ACM Conference on Principles, Systems and Applications of IP Telecommunications (IPTCOMM), pp.63–74, August, 2010.
19. A.Buschel, “Authentification in VoIP”, in Proceedings of the 2nd Workshop on Securing Voice over IP, June, 2005.
20. F.Cao and C.Jennings, “Providing Response Identity and Authentification in IP Telephony”, in Proceedings of the 1st International Conference on Availability, Reliability and Security (ARES), April, 2006.
21. K.Insu and K.Keecheon, “Secure Session Management Mechanism in VoIP Service”, in Proceedings of the Workshop on Ubiquitous Processing for Wireless Networks (UPWN), held in conjunction with the 5th International Symposium on Parallel and Distributed Processing and Applications (ISPA), pp.96–104, August, 2007.
22. H.Schmidt, C.-T.Dang, and F. J. Hauck, “Proxy-Based Security for the Session Initiation Protocol (SIP)”, in Proceedings of the 2nd International Conference on Systems and Network Communications (ICSNC), pp.42–47, August, 2007.
23. F.Wang and Y.Zhang, “A New Provably Secure Authentification and Key Agreement for SIP Using Certificateless Public-Key Cryptography”, Computer Communications, vol.31, pp.2142–2149, June, 2008.
24. K.Singh and S.Vuong, “Blase: A Mobile Agent Paradigm for VoIP Instruction Detection Systems”, in Proceedings of the 1st International Conference on E-Business and Telecommunication Networks (ICETE), August, 2004.
25. V.Casola, R.Chianese, A.Mazzeo, N,Mazzoca, and M.Rak, “A Policy-based Design Methodology and Performance Evaluation Framework for a Secure VoIP Infrastructure”, in Proceedings of the 1st International Conference on E-Business and Telecommunication Networks (ICETE), August, 2004.
26. V.Casola, M.Rak, A.Mazzeo, and N,Mazzoca, “Security Design and Evaluation in a VoIP Secure Infrastructure: A Policy Based Approach”, in Proceedings of the International Conference on Information Technology: Coding and Computing, pp.727–732, April, 2005.
27. S.Noccolini, R. G. Garroppo, S.Risi, and S.Ventura, “SI Instruction Detection and Prevention: Recommendations and Prototype Implementation”, in Proceedings of the 1st IEEE Workshop on on VoIP Management and Security (VoIP MaSe), pp.47–52, April, 2006.
28. K.Rieck, S.Wahl, P. Laskov, P.Domschitz, and K.-R. Miller, “A Self-learning System for detection of Anomalous SIP Messages”, in Proceedings of the 2nd International Conference on Principles, Systems and Applications of IP Telecommunications Services and Security for Next Generation Networks.(IPT-Comm), pp.90–106, July,2008.
29. B.Reynolds and D.Ghosal, “STEM: Security Telephony Enabled Middle box”, IEEE Communication Magazine, vol.40, pp.52–58, October, 2002.
30. D. T. Stott, “SAFENet: Server-based Architecture For Enterprise NAT and Firewall Traversal”, in Proceedings of the 2nd VoIP Security Workshop, June, 2005.
31. V. K. Gurbani, D.Willis, and F.Audet, “Cryptographically Transparent Session Initiation Protocol (SIP) Proxies”, in Proceedings of the IEEE International Conference on Communications (ICC), pp.1185–1190, 2007.







