The article focuses on the design and creation process of the automated integrated system for monitoring and control of home appliances and other things used in a person's everyday life. The following advantages of the system are taken into consideration: the control is carried out via the web-interface; the system structure is presented by a server and multiple client unit blocks.
Keywords: web-interface, monitoring, control system, client-server technology.
Modern century is characterized as a century of new developments. Different inventions occupy more and more part of our lives and it's difficult to imagine any sphere of a person's everyday life (social, economic, political and other ones) without innovations.
At present moment humanity is rapidly developing and at the same time the life pace is constantly increasing and requiring more and more time on everyday activities. As a result, sometimes those things which seem us to be the simplest and innocuous ones (household chores in particular) take up the greatest part of a person’s daily life which is, of course, limited by 24-hours period.
For example, during the whole week you were working quite hard and intensively, and when daily routines finally came to the end, on Friday evening or on Saturday or Sunday morning you decided to cook something delicious and tasty for yourself or maybe for your family members (like an apple pie or pancakes, for example). You go to the nearest supermarket, buy all the ingredients needed for you dish, return home and suddenly found out that you'd forgotten to buy milk for your cake. So you have to return to the store and buy a packet of milk.
Let us give another example from a person's everyday life. While leaving the house early in the morning you forgot to close the window curtains and all the windows of your room or flat or house face south. As a result, you return home in the evening and spend the rest of the day in a stuffy apartment and of, course, open all the windows of you dwelling to get some fresh air.
Or another situation: if you forgot to close the window for the night period it's very easy for you to catch a cold.
All unpleasant life situations mentioned above can be solved by developing an automated integrated system for monitoring and control of household objects through the web-interface.
General concept of the technical part
Technical part consists of a server and several types of universal client (peripheral) units of personal control panels. Each block contains a radio transmitter and a receiver operating on a free radio frequency 433 MHz, the aim of which is to establish a logical connection for sending commands and/or parameters between units (not only client-server but also client-client connection). This frequency is used in security system sensors [2].
For client units the following options are accessible:
- Discrete inputs/outputs with a function of width-pulse modulation (to control various relays and other low-power actuators;
- 8 analogue inputs (for getting data from analog sensors, for example, light and temperature sensors);
- 8/16 power outputs 12–48/220V with a width-pulse modulation function and built-in amperemeter (for controlling the power supply of electrical appliances such as lightning and ventilation);
- RFID-reader (plastic cards with magnetic labels);
- iButton key reader;
- IR transceiver (to provide the work of remote controls to all household appliances as well as for giving the opportunity to control and manage the functions of household appliances).
- GSM-module (for notifications sending and instructions receiving).
With a functional of modules mentioned above it's possible to provide a virtual management and control on any household appliance and realize exotic algorithms and conditions. For example:
- Events based on the functioning of your alarm-clock: to turn on a TV-program with news, to switch on the electric kettle on your kitchen table, or to start the car engine in cold Siberian winters.
- Morning or evening room/flat/house ventilation (for this procedure mechanical actuators are required.
- Turning off the TV-set and lightning in case the motion sensor doesn't work for a long time period (for example, a person fell asleep or on the contrary, if the person mustn't fall asleep).
- Automatic garage door opening in case the driver approaches the gates (based on RFID-labels).
- Control of the food amount on refrigerator shelves for the purpose of making the product shopping list or for the automatic product list making and its notification.
- Notification at the end of food readiness in the oven, microwave or in a multi-cooker. And many more other options which person's imagination and fantasy can create and a person, in his turn, can realize.
Some application variants are displayed in Figure 1.
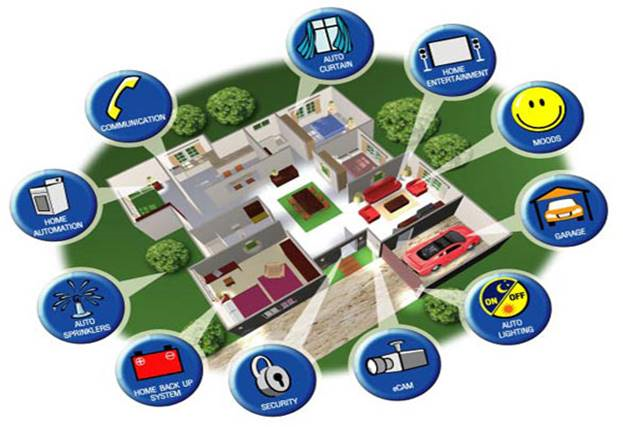
Fig. 1. Possible variants for system management
The server part
Final user needs an intuitively understandable web-interface for a simple implementation of such algorithms. Using web-interface provides for a user a possibility to set algorithms from any device with a web-browser and this makes the system more flexible.
The server part is implemented on a low-power computer with a conventional x86 processor architecture and operating system based on Linux kernel.
Linux kernel is created and distributed according to the development model of free and open software [3].
Using Linux, in the following, would provide the transition to computers/microcontrollers of other architectures such as ARM (used for example, in smartphones), MIPS (used at home in Wi-Fi routers).
In future, it’s planned to transfer a server part particularly to a Wi-Fi router because it significantly reduces energy consumption comparing with a computer which computational capacity is much higher than it is required and moreover, it would provide a price benefit.
Sample interaction organization of control system parts is shown in Figure 2.
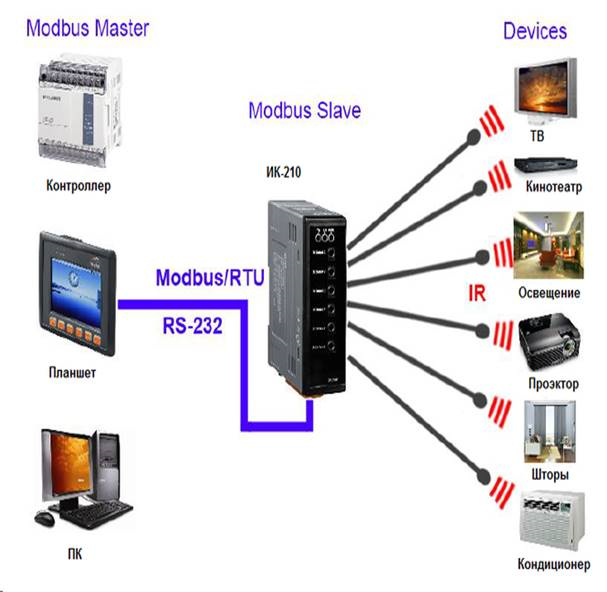
Fig. 2. Scheme of the system
Algorithms development is conducted on high programming language C++ as it provides a wide range of possibilities for development and doesn’t require any additional programs [1]. For each module an individual implementation algorithm will be created which matches the defined functions. It’s necessary to mentioned modules independency which provides the possibility to create certain module sets.
Summing up all mentioned above, we should say that a powerful idea was presented in the article. Its implementation consists in various modules for different purposes, the part of which has already been developed and another one is needed to be developed. At this stage a general idea and its basic implementation are founded, namely the wireless communication protocol and a communication protocol between modules. In the future, on the way of commercialization, these protocols will be encrypted for providing an adequate safety level. This system has its advantages: it can be easily expanded and implemented. At the same time, no difficulties exist in the development of new modules with a new functional as they interact by means of similar protocols.
The server part will be periodically renewed and expanded in terms of its functional and possible ready algorithms.
References:
1. Программирование в Linux с нуля. [Electronic data] — URL: http://www.opennet.ru/docs/RUS/zlp/zlp-prog.html.gz (дата обращения: 20.03.2015).
2. Статья GSM камера «ReVizor X9» с датчиками охраны и WEB-сервисом. [Electronic data] — URL: http://monitordv.ru/content/articles/449/ (дата обращения: 19.03.2015).
3. Debian — ОС на ядре Linux. URL: https://www.debian.org/index.ru.html (дата обращения: 23.03.2015).







