End-to-end encryption systems: problems of the information protection
Авторы: Апалько Ирина Юрьевна, Брянцев Арсений Вячеславович, Тазитдинов Арсений Альбертович
Рубрика: Информатика и кибернетика
Опубликовано в Техника. Технологии. Инженерия №2 (8) апрель 2018 г.
Дата публикации: 05.04.2018
Статья просмотрена: 91 раз
Библиографическое описание:
Апалько, И. Ю. End-to-end encryption systems: problems of the information protection / И. Ю. Апалько, А. В. Брянцев, А. А. Тазитдинов. — Текст : непосредственный // Техника. Технологии. Инженерия. — 2018. — № 2 (8). — С. 8-10. — URL: https://moluch.ru/th/8/archive/85/3271/ (дата обращения: 26.04.2025).
This paper investigates some methods of cryptographic protection of information during its transmission over insecure channels. Our work reveals the principle of encryption using a decentralized key distribution as a way to transform the processed in information systems original data into a cryptogram or a ciphertext. The trend of modern cryptography development and the actual problems of end-to-end encryption in the information space are also considered.
Key words: cryptographic protection of information, end-to-end encryption, asymmetric algorithms, decentralized key distribution.
В данной работе исследуются методы криптографической защиты информации при её передаче по открытым каналам связи. Раскрывается принцип шифрования с использованием децентрализованного распределения ключей, как способ преобразования обрабатываемых в информационных системах исходных данных в криптограмму или шифртекст. Рассматриваются также тенденции развития современной криптографии и актуальные проблемы сквозного шифрования в информационном пространстве.
Ключевые слова: криптографическая защита информации, сквозное шифрование, криптографические алгоритмы, асимметричные алгоритмы, децентрализованное распределение ключей.
Nowadays, one of the most important missions of the state is to provide information security. In modern society information has become the resource number 1. Therefore, information flows must be protected by all means.
There are some cryptographic methods of information protection including encryption which are used for this purpose. Encryption is the process of transforming the unprotected public information (a plaintext) into the protected private one, i.e. a ciphertext or a cryptogram. Today, the most promising way of encryption is end-to-end encryption. It implies the use of a key, which is known only to the participants of this process.
The essence of end-to-end encryption (E2EE) is in the fact that it’s impossible to intercept the message during its transmission or reception. E2EE is especially common for Internet communication, it is used by such applications as WhatsApp, Viber, Skype and Telegram.
In establishing communication between the two workstations, two keys are generated at each workstation: public and private (secret). The secret key is designed to decrypt the received information and it never leaves the local device, while the public key is transmitted through the open channel from the sender to the recipient. Only the sender can encrypt the message with his public key and the decryption is available only for the receiver who has a private key. In this case there is no loss of data.
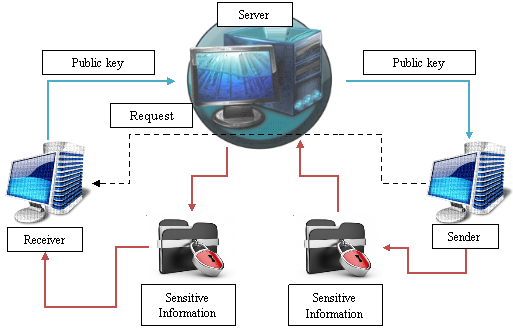
Fig. 1. The information transfer system with the decentralized key distribution
The communication system using the decentralized key distribution has a number of problems. The first problem is the loss of restricted information during its storage. It means that the information is protected only during its sending, while the receiving and sending points can be attacked. Thus, users of infocommunication networks, where E2EE is used, may be at risk.
The next problem is authorization of users who are the participants of the communication process. The problem of gaining access to private information consists of a process of authorizing users. Subscriber`s telephone number through SMS-message is used for authorization. This method of data transmission is based on SS7 (Signaling System # 7) technology, which was developed 40 years ago and according to the modern standards has weak security parameters. Thus, cryptanalysts have the ability to access information transfer devices and then directly access the information.
It is proposed to implement the principle of usage of conditional entropy in SS7 technology. However, it means to achieve an appropriate degree of uncertainty not by distortion of information by noise but by influencing information at some statistical element. As a result, secure authentication will be provided for a key and SMS-message. It should be borne in mind that the routing of the confirming data must be done through the channels that the servers provide.
It is necessary to add that in the current political situation in our country, such an encryption algorithm may be a threat to the information security of the Russian Federation. The Islamic state (IGIL, a terrorist organization banned in Russia) recruits the soldiers, using messengers (including Telegram) with end-to-end encryption. These means of communication can’t be intercepted or hacked.
This problem can be solved at the legislative level in the Russian Federation. Another solution of this problem is to provide access to the intelligence information processed in such information systems.
Thus, we can conclude that the uncontrolled usage of messaging by end-to-end data encryption poses a direct threat to the national security of the Russian Federation. Messenger creators believe that the secrecy of correspondence should be supported in full, but the problem is that terrorists can use it.
People do not understand that such free communication provides terrorists with the opportunity to secretly exchange data at all stages of training, including both the recruitment and the training of the recruits. Consequently, the structures that ensure security must control the Internet information.
References:
- Yo. Yazev. «Professional investigation. As enciphering in WhatsApp, iMessage and others», works 2016. [Electronic resource] — the access mode: https://www.iphones.ru/iNotes/595634 (Date of the address: 09/17/2017)
- Information portal «The Illustrated Self-instruction Manual on Information Security». [Electronic resource] — the access mode: http://samoychiteli.ru/document34384.html (Date of the address: 09/22/2017)
- Information Roem.ru portal, 2017 [Electronic resource] — the access mode: https://roem.ru/04–04–2017/246777/telegram-vs-isis/ (Date of the address: 10/10/2017)
- R. Rozhkov, S. Goryashko. «The State Duma asks FSB to block Telegram», 2015. [Electronic resource] — the access mode: https://www.kommersant.ru/doc/2855366 (Date of the address: 10/13/2017)
Ключевые слова
cryptographic protection of information, end-to-end encryption, asymmetric algorithms, decentralized key distributionПохожие статьи
Logo detection in images with a complex background using the contour information of images
Text detection has gotten a great attention as highly active application-oriented research area in computer vision, artificial intelligence, and image processing. In this article, we implement the algorithm for text logo detection in images with a c...
Transformed idioms in mass media (based on the national corpora of the English language anc and bnc)
This study investigates the occurrence of modified idioms in mass media, utilizing the comprehensive datasets of the American National Corpus (ANC) and the British National Corpus (BNC). Idioms hold considerable importance in language and communicati...
Excel-application «Select switches»
Modern electric power systems are a combination of complex objects with various factors of mutual influence, and therefore, to solve any issues relating to the design and subsequent operation of these objects, the development and use of specialized s...
To the question of practical use of ''Smart home'' system
The article focuses on the design and creation process of the automated integrated system for monitoring and control of home appliances and other things used in a person's everyday life. The following advantages of the system are taken into considera...
Features and problems of translation of media discourse texts
In this article, I will try to identify the characteristic features of the translation of media discourse on the material of modern television news. The article is devoted to the study of one of the urgent problems of media translation. In the contex...
Blockchain technology for through-life asset management in the aviation/space/automobile industry
The article examines Crypto Labels Reader for blockchain technology is poised as the future of digital transactions, infusing trust, efficiency and transparency into supply chains. But blockchains alone cannot ensure the authenticity of physical good...
Possibilities for technogenic waste for obtaining building materials
The article provides information about the negative impact of technogenic waste on the environment and efficiency of manufacturing building materials from them, which are necessary in the rapidly developing construction industry.
Way of providing information
The subject of the study is the method of information transmission. The objective of the study is to improve the efficiency of radio communication by increasing the spatial stealth. Analysis of spatial and temporal characteristics of radio channel ...
The role of teaching technologies in the development of speech and written speech in the English language
This article discusses the formation of language learning skills in the process of learning English to improve independent writing skills of students using information technology and the development of their creative abilities.
Designing a structured cabling system in a building
This article presents the concept of a structured cabling system, as well as its implementation through an existing network. The following questions should be considered: choice of technology and structure of the cable system, topology definition, op...
Похожие статьи
Logo detection in images with a complex background using the contour information of images
Text detection has gotten a great attention as highly active application-oriented research area in computer vision, artificial intelligence, and image processing. In this article, we implement the algorithm for text logo detection in images with a c...
Transformed idioms in mass media (based on the national corpora of the English language anc and bnc)
This study investigates the occurrence of modified idioms in mass media, utilizing the comprehensive datasets of the American National Corpus (ANC) and the British National Corpus (BNC). Idioms hold considerable importance in language and communicati...
Excel-application «Select switches»
Modern electric power systems are a combination of complex objects with various factors of mutual influence, and therefore, to solve any issues relating to the design and subsequent operation of these objects, the development and use of specialized s...
To the question of practical use of ''Smart home'' system
The article focuses on the design and creation process of the automated integrated system for monitoring and control of home appliances and other things used in a person's everyday life. The following advantages of the system are taken into considera...
Features and problems of translation of media discourse texts
In this article, I will try to identify the characteristic features of the translation of media discourse on the material of modern television news. The article is devoted to the study of one of the urgent problems of media translation. In the contex...
Blockchain technology for through-life asset management in the aviation/space/automobile industry
The article examines Crypto Labels Reader for blockchain technology is poised as the future of digital transactions, infusing trust, efficiency and transparency into supply chains. But blockchains alone cannot ensure the authenticity of physical good...
Possibilities for technogenic waste for obtaining building materials
The article provides information about the negative impact of technogenic waste on the environment and efficiency of manufacturing building materials from them, which are necessary in the rapidly developing construction industry.
Way of providing information
The subject of the study is the method of information transmission. The objective of the study is to improve the efficiency of radio communication by increasing the spatial stealth. Analysis of spatial and temporal characteristics of radio channel ...
The role of teaching technologies in the development of speech and written speech in the English language
This article discusses the formation of language learning skills in the process of learning English to improve independent writing skills of students using information technology and the development of their creative abilities.
Designing a structured cabling system in a building
This article presents the concept of a structured cabling system, as well as its implementation through an existing network. The following questions should be considered: choice of technology and structure of the cable system, topology definition, op...







